
Security continues to be an increasingly important concern in the design of modern systems. This white paper is based on secure boot which provides a foundation for the security architecture of a device. The paper attempts to introduce this concept and lists the processes involved, challenges faced, and best practices recommended.
Connected IoT devices can be found in every aspect of modern digital life, from autonomous and connected vehicles to medical devices, smart meters, and smartwatches.
While exposing a device to the external world, trust needs to be established in the system. Hence, security is fundamental to successful adoption of connectivity. Connected devices operate in an environment where attacks The first step to ensure security at the device level is through secure boot in an IoT-embedded system. can originate from anywhere. Devices must be capable of adapting to an evolving threat landscape. With the exponential increase in connected devices and the value of data stored in them, security has to be multifaceted, “baked-in” from the lowest levels of system-onchip (SoC) design through to the applications that run on them and in communications between devices and services.
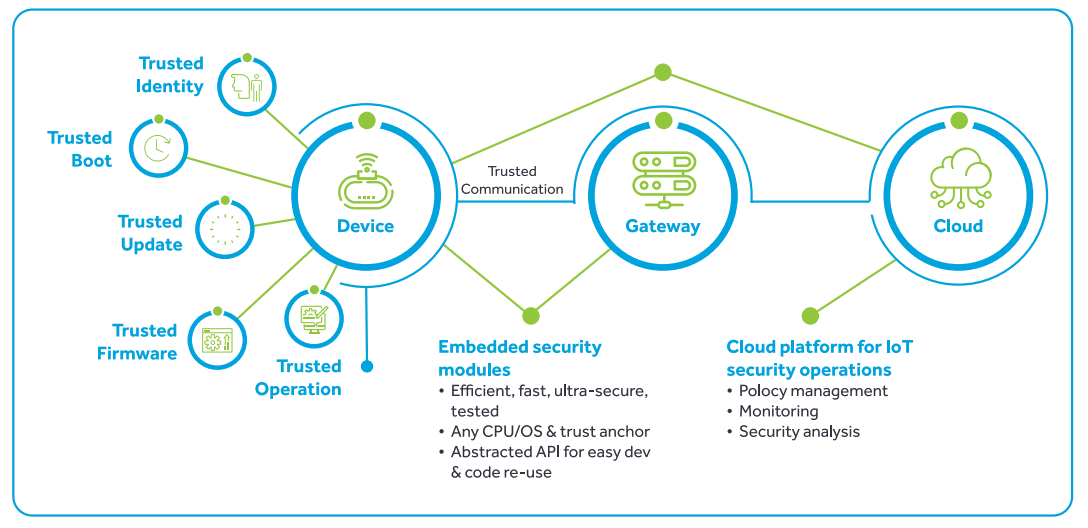
The first step to ensure security at the device level is through secure boot in an IoT-embedded system
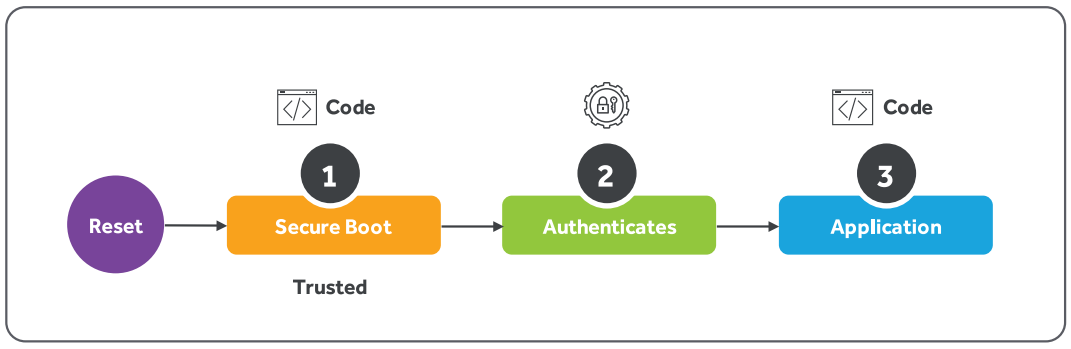
Secure boot is a process where your OS boot images and code are authenticated against a trusted hardware before they are allowed to be used in the boot process.
The hardware is set up beforehand such that it only authenticates code generated using security credentials you trust.
Secure boot is applicable for any single-use device, something that is not intended to be a general-purpose computing.

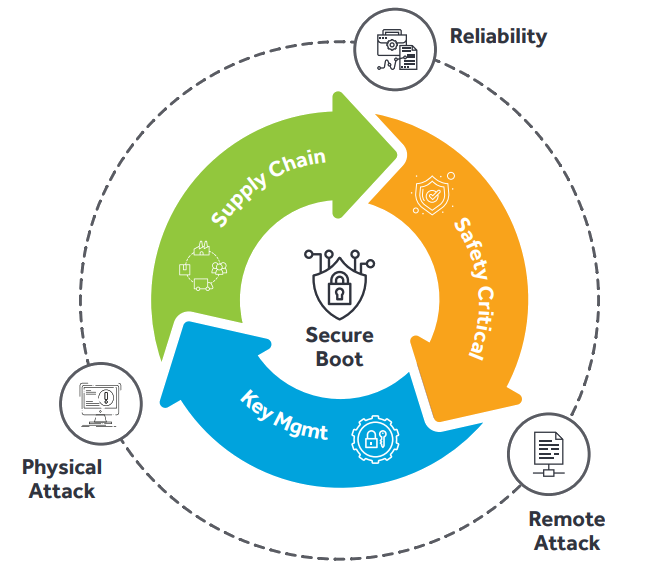
Secure boot is a key component of protection against physical and remote attacks and hardware and software failures.
The proliferation of IoT devices embedded into business-critical systems makes the use of secure boot an important factor in securing these devices and safeguarding their reliable operation. Any malicious code inserted into the device could make this device part of a botnet or be used as a launching pad for attacks targeting other, more sensitive systems.
Secure boot ensures a root of trust that is accomplished using a hardware state machine. The goal of a hardware root of trust is to verify that the software installed in every component of the hardware is the intended software. This way you can verify and know without a doubt whether a machine's hardware or software has been hacked or overwritten by an adversary. Thus, it helps prevent supply chain attacks, physical attacks, cloud provider vulnerabilities in hardware components, and other attack vectors by ensuring hardware and software integrity.
Verifying the authenticity of a bootloader is crucial for assuring and executing the rest of the boot process. Verification of the bootloader executable file is done using public/private keys. During secure development, the bootloader is digitally signed with the manufacturer’s private key.
When the bootloader firmware is installed on the device, it is checked against the embedded public key on the device to confirm that it is genuine. The same process is repeated whenever the device boots or installs an update.
Once the bootloader file is checked successfully for authenticity, the secure boot process checks the validity of the operating system and other functional applications. The signed application code is verified against the embedded public key to ensure it is genuine. If the operating system and the applications are assured, they can start running.
The series of steps involved in the secure boot process is depicted below.
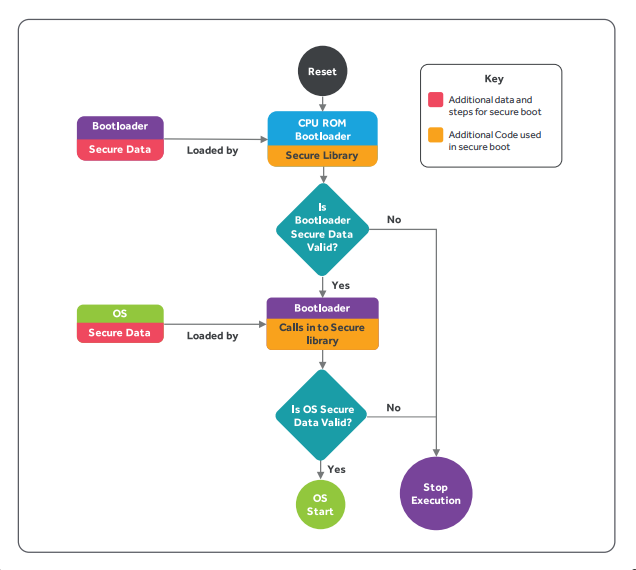
To summarize, the device start-up process is initiated by a trusted bootloader file and every phase is run only after the previous phase is verified for authenticity and started successfully.
Secure boot is based on the hardware root of trust offered by OEMs.
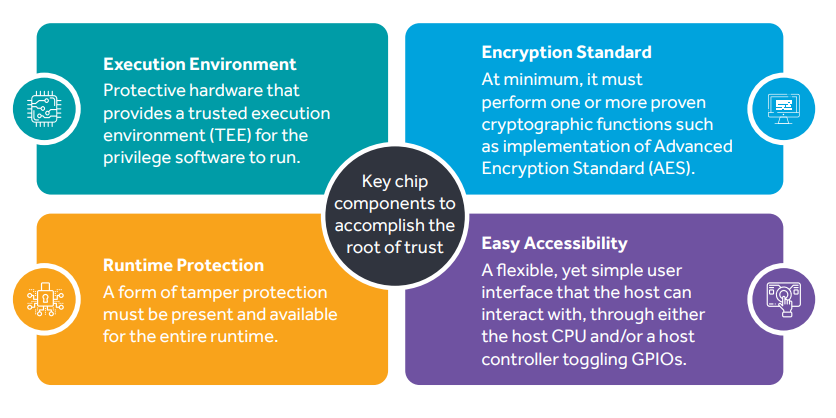
The two major implementation steps in building the secure boot process and are outlined below.

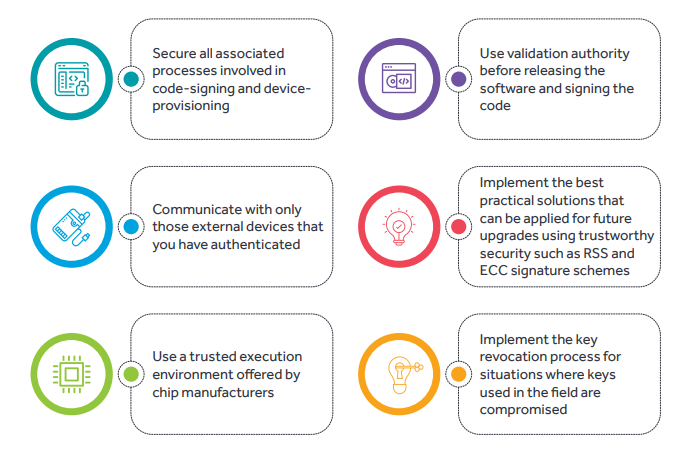
When properly configured, secure boot lays the foundation for a root of trust and is a requisite for system security. We believe security is an integral part of IOT adoption and connected systems. Secure boot implementation requires specific hardware capabilities. Therefore, it is critical this be factored into the early-stage design phase. Cyient offers a comprehensive range of services and solutions for securing embedded IOT devices across multiple industry verticals.
Cyient (Estd: 1991, NSE: CYIENT) is a leading global engineering and technology solutions company. We are a Design, Build, and Maintain partner for leading organizations worldwide. We leverage digital technologies, advanced analytics capabilities, and our domain knowledge and technical expertise, to solve complex business problems.
We partner with customers to operate as part of their extended team in ways that best suit their organization’s culture and requirements. Our industry focus includes aerospace and defense, healthcare, telecommunications, rail transportation, semiconductor, geospatial, industrial, and energy. We are committed to designing tomorrow together with our stakeholders and being a culturally inclusive, socially responsible, and environmentally sustainable organization.
For more information, please visit Cyient
Cyient (Estd: 1991, NSE: CYIENT)delivers Intelligent Engineering solutions for Digital, Autonomous and Sustainable Future
© Cyient 2024. All Rights Reserved.