IoT is playing a key role in connected and telehealth care where patient monitoring and smart health management are provided remotely. Such technologies not only improve the patient experience but also reduce operational costs significantly. As health care providers and medical device manufacturers introduce more and more connected devices to the market, the challenge is to Implement these new technologies such that they do not violate data privacy while protecting patients and operators from cybersecurity risks. Medical device manufacturers are also responsible for identifying cyber security risks (malware, hijacking, unauthorized access) associated with their devices and putting appropriate risk mitigations in place to address patient safety and device performance.

The biggest challenges networked medical devices face are to secure the interoperability, reduce the cybersecurity related threats to a patient’s personal and health information, and ensure safety of patients and operators from illness, injury, or death. In contrast, the challenges in standalone medical devices are to safeguard the physical access, software, firmware, and the operating system from malicious damage or disruption. Cyber attackers can use compromised medical devices to attack other portions of an organization’s network. Cybersecurity vulnerability can potentially cause a device recall due to security issues.
This paper describes the conceptual solution for implementing a robust framework to identify, manage, and recover from cybersecurity risks by following regulatory guidelines, standards, and best practices
To address cybersecurity challenges in connected medical devices, healthcare providers must introduce a robust cybersecurity framework to manage risks. A clear understanding of the health care organization’s business drivers and security considerations specific to its use of technology are required to assess the risks. As each organization’s risks, priorities, and systems are
unique, the tools and methods used to achieve the outcomes described by the framework will vary. By utilizing these framework processes an organization can leverage the framework to identify opportunities to strengthen and communicate its management of cybersecurity risk while aligning with industry practices. The framework is a risk-based approach to manage cybersecurity, and features the following components:
Framework: This control family consists of five concurrent and continuous functions as depicted in Figure 1. These functions— Identify, Protect, Detect, Respond, Recover— organize cybersecurity activities such as asset management, identity management and access control, and detection processes.
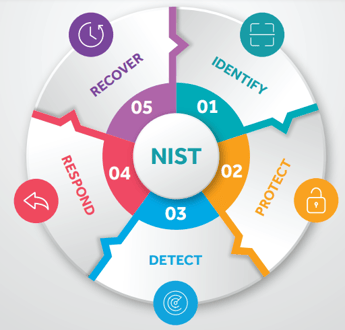
Figure 1: National Institute of Standards and Technology framework
Develop organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities
The table below illustrates the mapping between framework controls with General Data Protection Regulation (GDPR), International Organization of Standardization 27001 (ISO27001), and Health Insurance Portability and Accountability Act (HIPAA) controls that can be used by medical device manufacturers to design and implement a robust cybersecurity framework.
Asset Management
Business Environment
Governance
Risk Assessment
Risk Management Strategy
Article 32: Security of Processing— establish appropriate technical and organizational measures to ensure a level of security appropriate to the risk of data being processed.
Article 35: Data Protection Impact Assessment— establish data protection impact assessment mechanism to assess the impact
A.5 Information Security: Establish management direction and support for information security in accordance with business requirements and relevant laws and regulations.
A.6 Organization of Information Security: Establish a management framework to initiate and control the implementation and operation of information security within the organization.
§164.306 Security Standard: Confidentiality, integrity, and availability of all electronic protected health information (ePHI) the covered entity or business associate creates, receives, maintains, or transmits.
Develop and implement the appropriate safeguards to ensure protection of assets. The table below illustrates the mapping between the framework control family and regulatory controls.
Access Control
Awareness and Training
Data Security
Information Protection Processes and Procedures
Maintenance
Protective Technology
Articles 5 and 25: Rules and guidelines for applying data protection by design and by default.
Article 24: Data protection policies.
Article 30: Record of processing activities.
Article 32: Data encryption at rest and in transit.
Article 35 and 36: Documents for Data Protection Impact Assessment and prior consultation.
A.8 Asset Management: To identify organizational assets and define appropriate protection responsibilities.
A.9 Access Control: To limit access to information and information processing facilities.
A.10 Cryptography: Ensure proper and effective use of cryptography to protect the confidentiality, authenticity and/or integrity of information.
A.11 Physical and Environmental Security: Prevent unauthorized physical access,
A.12 Operational Security: Ensure correct and secure operations of information processing facilities.
A.13 Communications Security: Ensure protection of information in networks.
§164.306 Security Standard: Protection of ePHI against anticipated threats or hazards.
§164.308 Access Authorization: Implement policies and procedures for granting access to electronic protected health information and prevent security violations.
§164.310 Physical Safeguards: Implement policies and procedures for facility and workstation access controls to limit physical access to its electronic information systems
§164.312 Technical Safeguards: Implement access control policies for electronic information stored or in transit. Policies for right authentication. Mechanism to encrypt electronic protected health information.
Develop and implement appropriate activities to identify the occurrence of a cybersecurity incident. The table below illustrates mappings between the framework control family and regulatory controls.
Anomalies and Events
Security Continuous Monitoring
Detection Processes
Article 32: Security of Processing—establish appropriate technical and organizational measures to ensure a level of security appropriate to the risk of data being processed.
A.12. Operations Security: Ensure that the IT systems, including operating systems and software, are protected against data loss. Additionally, record events and generate evidences that can be used to detect, track, and trace the loss of information.
§164.308 Administrative Safeguards: Implement policies and procedures to detect security violations.
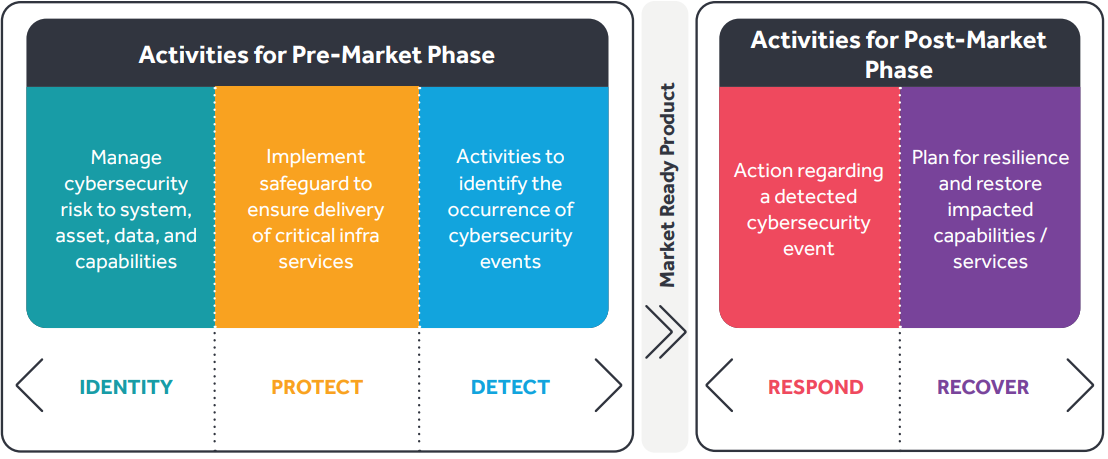
Figure 2: Pre-Market Submission
In support of Pre-Market submission (illustrated in Figure 2), the table below describes what the medical manufacturer should do before the device is marketed and sold to customers. It is recommended that the manufacturer integrate risk management during the development of the medical device and provide documentation on submission for Food and Drug Act/FDA approval.
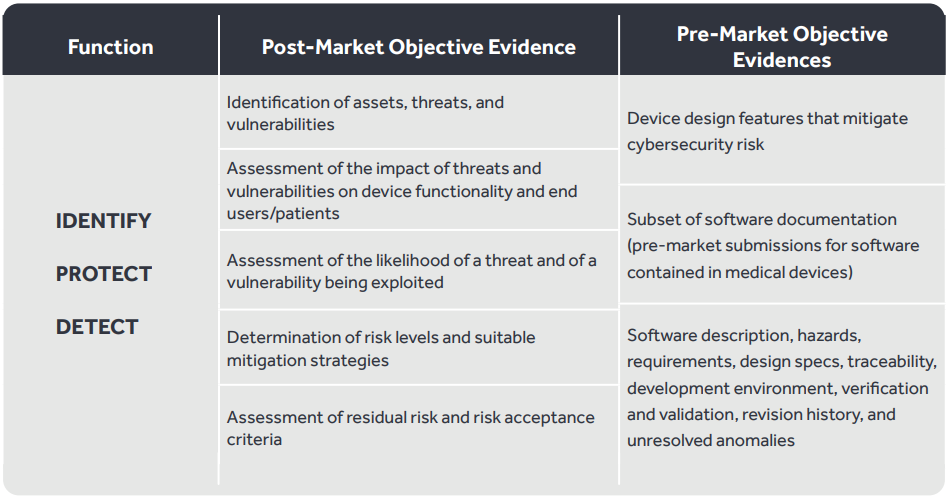
Develop and implement appropriate activities when facing a detected security event. The table below illustrates the mappings between the framework control family and regulatory controls.
Response Planning
Communications
Analysis
Mitigation
Improvement
Articles 33 and 34: Guidelines and processes to notify in case of personal data breaches.
A.16 Information Security Incident Management: Ensure a consistent and effective approach to the management of information security incidents, including communication on security events and weaknesses.
§164.308 Administrative Safeguards: Data backup and contingency plan for retrieval of electronic protected health information.
§164.308 Administrative Safeguards: Implement policies and procedures to correct security violations.
Develop and implement appropriate activities to restore any capabilities or services that were impaired due to a security event. The table below illustrates the mappings between the framework control family and regulatory controls.
Recovery Planning
Improvements
Communications
Article 32: Security of Processing—establish appropriate technical and organizational measures to ensure a level of security appropriate to the risk of data being processed.
A.17. Information Security Aspects of Business Continuity Management: Ensure the continuity of information security management during disruptions and the availability of information systems.
§164.308 Administrative Safeguards: Disaster recovery plan to restore any loss of data.
§164.310 - Physical Safeguards: Data backup and storage for retrieval of protected health information. Contingency plan that allows facility access in support of restoration of lost data under the disaster recovery plan.
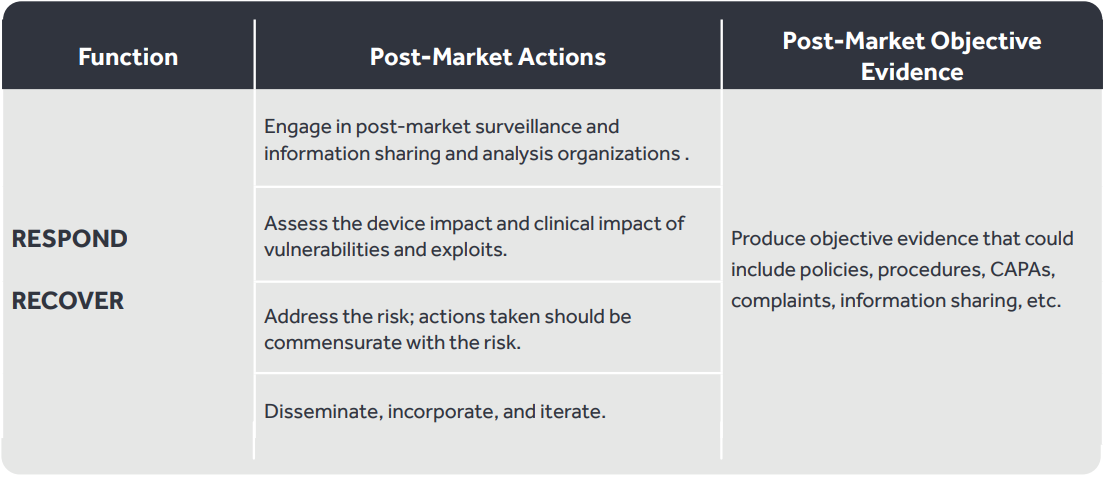
In support of the Post-Market phase (illustrated in Figure 1), the manufacturer must take action for a medical device after it is sold to the customers. The table below describes what the medical manufacturer should do after the device is marketed and sold to customers. It is recommended that manufacturers continually monitor cybersecurity for products already on the market to account for new threats and vulnerabilities.
Medical device manufacturers need to ensure they develop an ecosystem that keeps all sensitive patient-related data protected and in accordance with current regulations. Listed below are best practices to be considered for implementing a robust cybersecurity infrastructure for medical devices that would protect from cyber attacks.
Medical device interfaces may include hardwired connections and/or wireless communications (Wi-Fi, Ethernet, Bluetooth, USB, etc.) and it is important to consider how data transfer to and from the device is secured to prevent unauthorized access, modification, or replay.
The medical device manufacturer should consider protecting data that is stored on or transferred to/ from the device using encryption.
The medical device manufacturer should evaluate the system-level architecture to determine if design features are necessary to ensure data nonrepudiation (e.g., supporting an audit logging function). They should also consider risks to the integrity of the device such as unauthorized modifications to the device software and controls such as anti-malware to prevent viruses, spyware, ransomware, and other forms of malicious code being executed on the device
The medical device manufacturer should consider user access controls that validate who can use the device or allow granting of privileges to different user roles.
The medical device manufacturer should consider controls to prevent an unauthorized person from accessing the device (e.g., physical locks or physically restricting access to ports).
Medical device manufacturers should establish and communicate a process for implementation and deployment of regular updates. They must have a plan to respond to software updates or outdated operating environments outside their control.
The medical device manufacturer should consider design features that will allow the device to detect, resist, respond, and recover from cybersecurity attacks to maintain its essential performance.
In line with the megatrends of “Future Mobility” and “Human Well-Being,” medical devices need to be mobile and connected. This helps in collection, processing, and presentation of huge volumes of data such that it is easy to ingest, drives better decision-making, and significantly improves healthcare delivery. At the same time, networked/connected smart devices pose cybersecurity risks for the entire healthcare ecosystem. Also, the megatrends of “Intelligent and Connected Products” and “Next-Gen Connectivity Solutions” mandate that devices have inbuilt features related to patient data protection, security policies, best practices, and processes that must be continually updated and evaluated. It is highly recommended that organizations consider these guidelines, best practices, and compliances based on industry standards early in the development cycle, preparing for pre-market submissions, and post-market surveillance.
Cyient (Estd: 1991, NSE: CYIENT) is a leading global engineering and technology solutions company. We are a Design, Build, and Maintain partner for leading organizations worldwide. We leverage digital technologies, advanced analytics capabilities, and our domain knowledge and technical expertise, to solve complex business problems.
We partner with customers to operate as part of their extended team in ways that best suit their organization’s culture and requirements. Our industry focus includes aerospace and defense, healthcare, telecommunications, rail transportation, semiconductor, geospatial, industrial, and energy. We are committed to designing tomorrow together with our stakeholders and being a culturally inclusive, socially responsible, and environmentally sustainable organization.
For more information, please visit www.cyient.com
Cyient (Estd: 1991, NSE: CYIENT)delivers Intelligent Engineering solutions for Digital, Autonomous and Sustainable Future
© Cyient 2024. All Rights Reserved.