- 2026-Feb-17
Securing Virtual Machines in a Cloud Computing Environment
Written by Anoop Kodipurayil 13 Apr, 2023
The COVID-19 pandemic inadvertently expanded the cloud computing market, which has seen a massive spike in cloud adoption, infrastructure, spending, and development. According to a recent survey by Statista, 60% of all corporate data is now stored in the cloud. With the global cloud storage market expected to increase from $83.41 billion in 2022 to $376.37 billion by 2029, an annual growth rate of 24.0%, securing virtual machines (VMs) in a cloud computing environment has become a necessity.
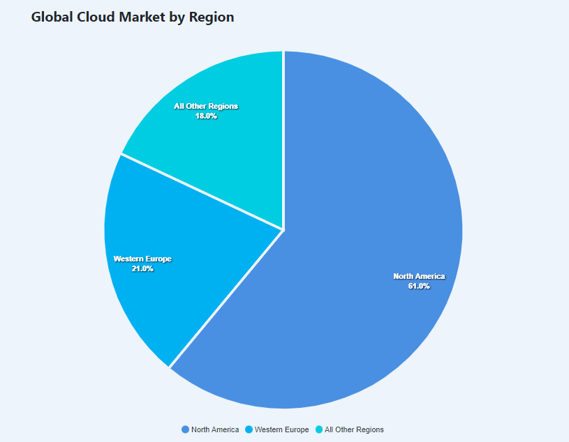
Stats by Cloudwards
As cloud computing continues to gain popularity, the use of virtual machines has become increasingly common. Virtual machines allow for greater flexibility and cost savings but present new security challenges. With sensitive data and applications being hosted on virtual machines, it is crucial to ensure they are properly secured. This entails key steps, from selecting the right security measures to implementing best practices for user access and network security.
Securing a VM: Best Practices
Securing a virtual machine in a cloud environment requires careful planning and implementation of various security measures. Here are the essential steps:
- Implement strong access controls for VMs using multi-factor authentication, strong passwords, and role-based access control (RBAC) to ensure only authorized users can access your VM.
- Use encryption to protect data stored on the VM. This includes using encryption for data at rest and data in transit. We can use encryption protocols such as HTTPS, SSL/TLS, and SSH to protect data in transit. Some common methods to enable encryption at rest include disk encryption, file-level encryption, and database-level encryption.
- Use vulnerability management and patching to regularly update software and operating systems with the latest security patches and updates. This will help to close any known vulnerabilities in the system.
- Use endpoint protection such as antivirus/EDR and HIDS solutions to protect the VM from malware and other security threats. Ensure that the endpoint security software is up-to-date and configured correctly.
- Use security monitoring regularly for any unusual activities or vulnerabilities. Use tools such as intrusion detection systems (IDS) and security information and event management (SIEM) to monitor the VM and detect any security incidents.
- Use a backup as regular data backups can help protect against data loss due to security incidents or other disasters. By backing up data on a separate location or device, the data can be restored if the original data is lost or becomes corrupted.
- Follow security hardening and best practices and industry-specific security requirements and regulations. The National Institute of Standards and Technology (NIST) and Center for Internet Security (CIS) maintain standards for system hardening best practices.
Following these steps ensures that your virtual machine is secure, but it's important to remember that security is an ongoing process, and you should regularly review and update our security measures to keep up with new threats and vulnerabilities.
Benefits of Virtualized Security
Virtualized security, which refers to the use of security solutions designed specifically for virtualized environments, offers several benefits over traditional security solutions. From greater flexibility and scalability to enhanced threat detection and response, virtualized security solutions provide organizations with the tools they need to better protect their virtualized infrastructure. With cybersecurity becoming one of the most tenacious concerns of every organization, the threat increases multifold with a virtual machine in the infrastructure.
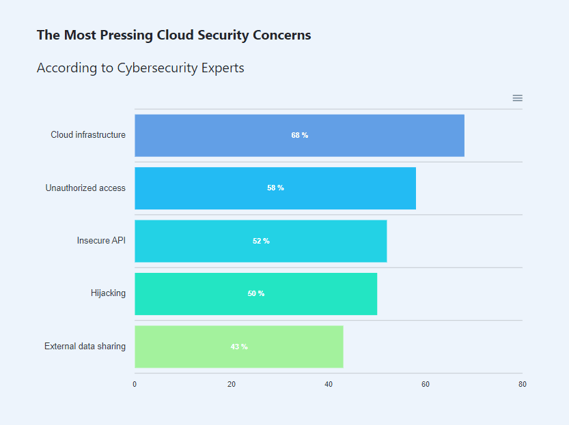
Stats by Cloudwards
In such scenarios, the security of company data and other assets becomes precarious, and a virtual mesh to secure the network perimeter becomes crucial. Businesses can mitigate the entry of malicious malware by establishing dedicated security resources within a cloud construct and customized firewall settings. Here are some benefits that virtualized security offers to help businesses achieve better security for their data and improve scale and efficiency:
- Protection of sensitive data: Virtual machines often store sensitive data such as personally identifiable information (PII), financial data, and intellectual property. If these virtual machines are not adequately secured, they can become easy targets for cybercriminals, who may steal or misuse this sensitive data.
- Compliance requirements: Many industries have compliance requirements that mandate the protection of sensitive data. For example, the healthcare industry must comply with HIPAA regulations, while financial institutions must comply with PCI DSS standards. Failure to comply with these regulations can result in legal and financial penalties.
- Business continuity: Virtual machines play a critical role in many organizations, and their downtime can cause significant disruptions to business operations. Securing virtual machines helps prevent downtime due to security breaches or other incidents, ensuring business continuity.
- Reputation management: Security breaches and data theft can damage an organization's reputation and erode customer trust. By securing virtual machines, organizations can protect their reputation and demonstrate their commitment to data security.
- Cost savings: Security breaches and data theft can be expensive, both in terms of financial losses and the cost of remediation. Organizations can avoid these costs and prevent future security incidents by implementing security measures to secure virtual machines.
Securing virtual machines in a cloud computing environment is a critical aspect of protecting sensitive data, complying with regulations, ensuring business continuity, maintaining reputation, and saving costs. Organizations can significantly reduce the risk of security breaches and data theft by implementing proper security measures, configuring user access and permissions, and ensuring network security. Regularly applying security patches and updates, monitoring for security threats, and choosing a secure virtual machine image are also important steps in securing virtual machines. By adopting virtualized security solutions and best practices for virtual machine security, organizations can better protect their virtualized infrastructure and safeguard their sensitive data and applications.
About the author
Anoop K is a Security expert with 14 years of industry experience in various domains of Cyber Security such as Infrastructure & Cloud Security and SOC. He has managed and executed many projects with varying degrees of complexity across various countries and different operating environments. He has deep expertise in Cloud infrastructure & security, Security operations, Security Orchestrations & Automation.
.png?width=774&height=812&name=Master%20final%201%20(1).png)




