- 2026-Feb-17
Software-Defined Automotive Cybersecurity: More Than in-Vehicle and Cloud
Written by Harsha Archak 06 Jul, 2022
Cybersecurity is of critical importance in a digital world. When it comes to self-driving cars, or vehicles with advanced driver assistance systems (ADAS), the stakes are a bit higher. If someone hacks into your vehicle, they could disable it, or worse, crash it and possibly harm passengers and bystanders. This risk is a difficult one to tackle but it can be managed.
Autonomous vehicles present hackers with a unique opportunity: they can physically interact with a target vehicle without having to buy or steal it. Once physically plugged in, hackers could use increasingly ubiquitous ADAS features to control the car with disastrous consequences.
Autonomous vehicles present hackers with a unique opportunity: they can physically interact with a target vehicle without having to buy or steal it. Once physically plugged in, hackers could use increasingly ubiquitous ADAS features to control the car with disastrous consequences.
Autonomous vehicles present hackers with a unique opportunity: they can physically interact with a target vehicle without having to buy or steal it. Once physically plugged in, hackers could use increasingly ubiquitous ADAS features to control the car with disastrous consequences.
CAN (Controller Area Network) Vulnerability Attacks
Being in the car allows the hacker to hack into the vehicle’s CAN, an internal network that allows for communication between components. Once someone has access to this network they can use it with disastrous effect. With that ECU out of the way, they could hijack the entire system instead of interfering with individual components. Some hackers have also been able to use the CAN network to simply disable components. They corrupt data coming in from sensors or microcontrollers to the central processor, and eventually, the primary controller thinks the component is damaged and cuts it off. There’s always the risk that your components can fail in the field by chance, but this kind of attack could shut down all ADAS features simultaneously.
Attack Vectors
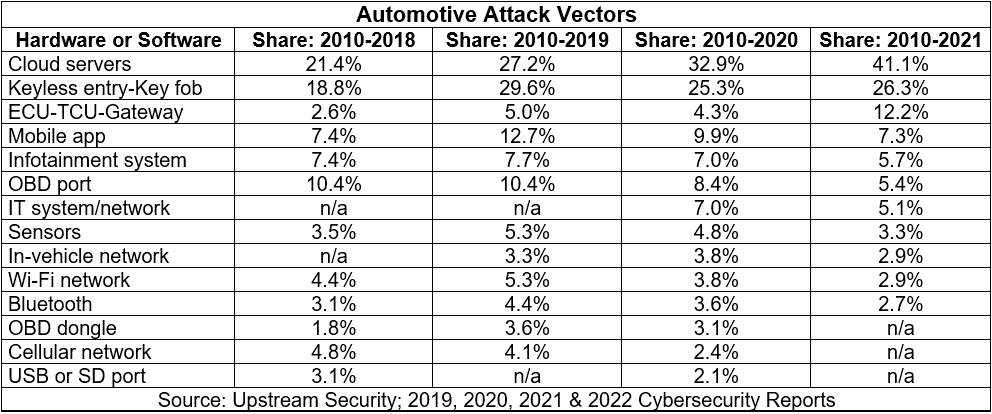
Once inside a car’s network, a hacker could use the CAN network’s security flaws to tamper with any part of the vehicle controlled by computers. In ADAS-enabled cars, everything from the brakes to steering can be controlled by ECUs, and this poses a grave risk because the user may not be able to override computer controls physically.
Once inside a car’s network, a hacker could use the CAN network’s security flaws to tamper with any part of the vehicle controlled by computers. In ADAS-enabled cars, everything from the brakes to steering can be controlled by ECUs, and this poses a grave risk because the user may not be able to override computer controls physically.
A self-inflicting attack is far harder to detect and easily circumvents existing intrusion detection systems that look for the anomalous frames that represent malicious communication within a car's network. It waits for a target component to send one of those frames, and then sends its own at the same time with a single corrupted bit that overrides the correct bit in the original frame. When the target component sees that it has sent an incorrect bit, the CAN protocol requires that it issue an error message "recalling" that faulty message. Repeat the attack enough times—car components tend to exchange messages—and those repeated error messages trick the component into telling the rest of the network that it's defective and cutting itself off from further communication.
An attacker could randomize the pattern of error messages to make detection more difficult. And those errors are also difficult to distinguish from actual malfunctioning components. To counteract this, the OEMs’ best defense is to segment their networks to isolate critical safety components from ones that might be accessible to hackers and even consider adding a layer of encryption to the CAN protocol to make messages more difficult to mimic.
Cyber Legislation: WP.29 & ISO/SAE 21434
Two cybersecurity regulations will significantly impact all aspects of automotive cybersecurity: WP.29 and ISO/SAE 21434.
2022 will be the first year, these two standards regulate automotive software.
A vital requirement of these cybersecurity standards and regulations is that each vehicle must be secured throughout its entire lifecycle from development and production and across all vehicle customer use phases. With this, OEMs and their supply chains must include multi-layered cybersecurity solutions to protect against current and future cyberattacks.
Defending against Attacks
The first thing that can protect cars is a culture of digital security. Once electronic defense is mandated, one should also consider securing entry points, consolidating components, and attack detection.
Many cars now use up to 100 separate ECUs for their systems. As ADAS becomes more common, many manufacturers are combining far-flung ECUs into a single microcontroller unit (MCU). This is primarily to increase the processing power available, but also serves a security purpose. It’s easier to defend a single MCU against attack than 100 ECUs. However, if a single MCU is used, the consequences can be worse if it’s compromised.
It’s difficult to protect against an intrusion without knowing it. Hence, it’s critical that the system must be able to check itself for malicious code. Hackers can sometimes gain access to a sensor-based system by injecting code into a data stream. If the processor can check the code it’s running against the original code, one may be able to detect and interrupt an incursion.
High Stakes Security and Precautions
The stakes are high when it comes to securing autonomous vehicles. First, you must physically secure your car’s systems to prevent a rider from accessing them. Then you must focus on software safety by implementing fail-safes and self-checks. Building a fail-safe system is essential to reduce an intrusion's repercussions. Two good ways to do this are to limit cascading failures and allow for over-the-air patches:
1. Masking components can mitigate some of that risk, as it’s more difficult for a hacker to enter a system if they don’t know what kind of components they’re dealing with.
2. Also, using tamper-evident tape can help you know when someone has opened something they shouldn’t have.
Memory protection units (MPUs) are used to guard against cascading failures in MCUs. This kind of system should be put in place to guard against cascading exploits. If an attacker gains control of a single ECU, it’s possible they could cause it to fail and trigger a chain reaction that affects the car. It’s a good idea to isolate systems enough that a purposeful failure in one cannot cause a total system failure.
It is much more likely to foil hacking attempts with software than with physical protection. Software checks to ensure components are still working can alert the system to intrusions. If the ECU domain controller is in update mode while driving, it is known that there’s a problem, and you can park the car until the issue is fixed. Checking components can help foil attacks like the disabling hack mentioned earlier. Someone may have used the CAN network to trick the processor into thinking sensors aren’t working. If those sensors are self-checking, they can tell the controller that they are, in fact, operational and trigger some fail-safe. Mitigation can be done if an attack is happening. The problem occurs when a known breach is unprepared and lets the hacker run amok within the system. Segmenting the system as much as possible will prevent cascading failures. If someone hacks into the entertainment system in the car, they should not be able to use it to disable the entire system.
Case Study: Machine Learning Can Detect and Prevent Attacks
As with all machine learning applications, the first step to deploying artificial intelligence to combat security risks in autonomous vehicles is collecting and storing the right data. If a car’s internal network is monitored using a platform capable of storing and analyzing logs, the vehicle itself can detect malicious activity and prevent attacks―or, at the very least, alert drivers and mitigate their impact.
One example of an effective platform capable of storing and analyzing logs is Elasticsearch, which is widely used in security. The chart below illustrates how a car’s user logs could flow into an Elasticsearch database, which would enable algorithmic detection of potential exploits.
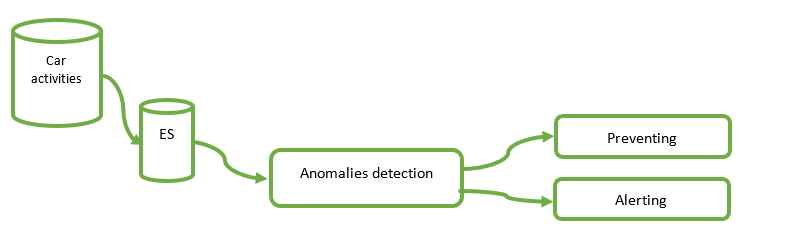
An example of a learn-and-prevent device that works in a vehicular context is the anti-hacking solution developed by Miller and Valasek. It is an intrusion-detection system for vehicles with certain automated features.
The device is based on a general-purpose NXP microcontroller, with a simple board plugged into the OBD2 port. It works by operating in an observation mode for the first few minutes of a drive, allowing the device to capture a vehicle’s typical data patterns. Then, it switches to detection mode to monitor the system for anomalies, such as an unusual flood signal or command. If it spots a “bad” signal, it puts the car into “limp mode,” essentially shutting down its network and disabling some functions such as power steering and lane assist until the vehicle restarts.
After the anomaly is detected, two different actions can be triggered: prevention and alert.
The prevention module is used to “tell” the car it should ignore the rogue commands, and it can be used to block attackers trying to use the same approach. The alert module is used to send (or display) notifications in real time, allowing drivers to take action or automatically inform the authorities of the attack. This module can be extended with the dashboard integrated into the car.
Long-Term Solutions to Protect against Exploits and Attacks
- Network segmentation: By altering the topology or segmenting a CAN in a vehicle, targeted error-flooding can be stopped from affecting a specific system.
- Regulated OBD2 port access: Creating a unique hardware key or password to open the case where the port is physically located may protect against illegal and unauthorized devices being introduced to the CAN. The implementation of a software-level authentication to allow traffic from and to the port can also be considered.
- Encryption: Encrypting CAN frame ID fields can prevent attackers from identifying CAN frames to target, thus resulting in a noisier and much more detectable attack pattern.
As a technology services provider, Cyient works closely with the industry experts, equipment manufacturers, and aftermarket customers to align with automotive industry trends through our focus areas of megatrends "Intelligent Transport and Connected Products," "Augmentation and Human Well-Being," and "Hyper-Automation and Smart Operations.
.png?width=774&height=812&name=Master%20final%201%20(1).png)




